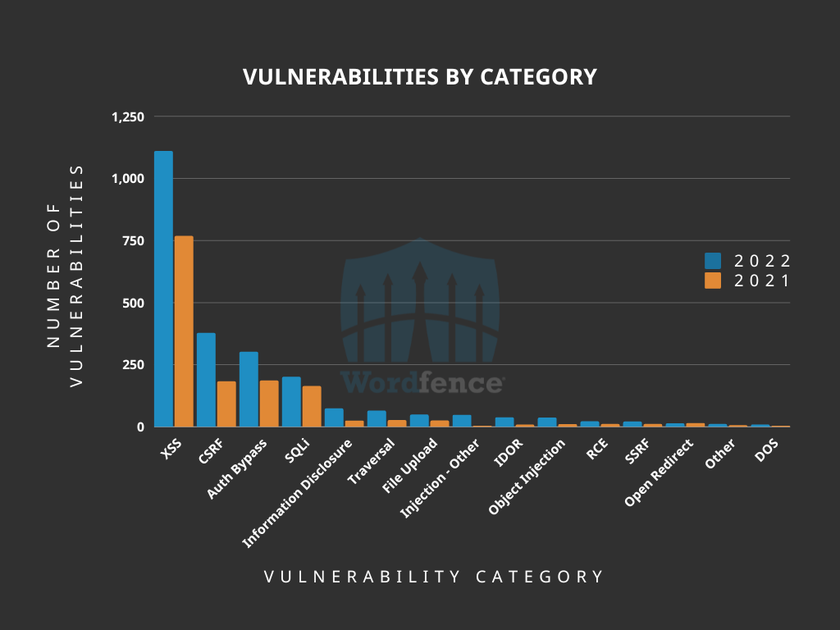
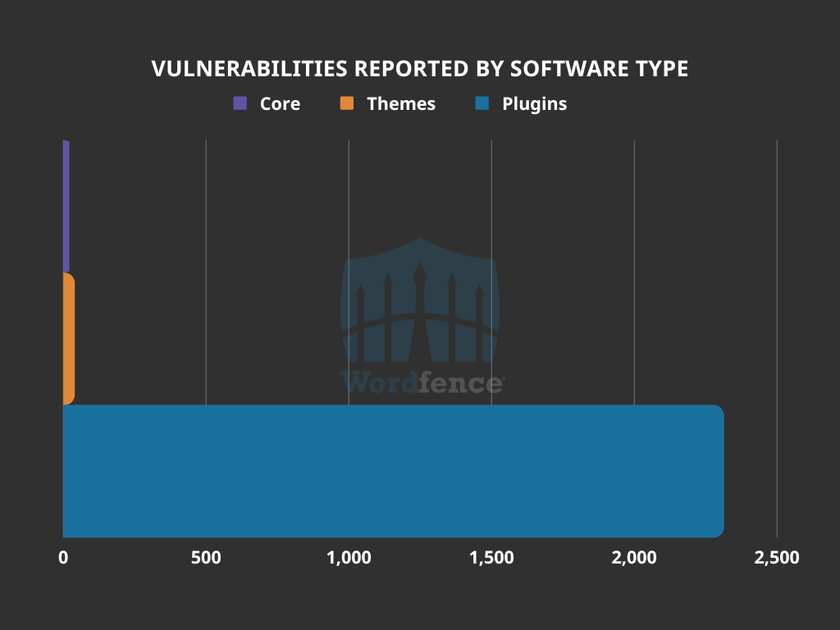
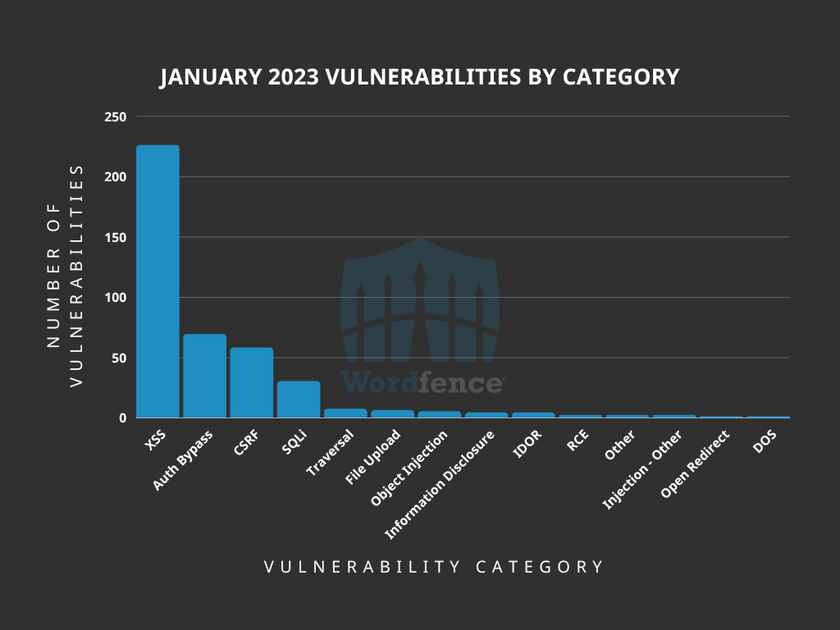
The Wordfence 2022 State of WordPress Security Report was released on January 24th, 2023. One area that was reviewed in the report were the vulnerabilities disclosed in 2022. Keeping in mind that some vulnerabilities affected multiple plugins, themes, and WordPress core, a total of 2,370 vulnerabilities were reported in 2022. The top five vulnerability categories were Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), authorization bypass, SQL Injection (SQLi), and information disclosure. While the statistics sum up what was in the report, the story does not end there.
The report shows some similarities, as well as distinct differences, to the prior year. This is not uncommon, as WordPress development, both for core and for plugins and themes, potentially includes years’ worth of legacy code, as well as newer code that fits updated coding standards. This tends to have the effect of increasing the number of potential vulnerabilities, while also creating new ways for vulnerabilities to exist.
In addition to changes in code, one major factor in the increase of vulnerability reports in 2022 was likely the fact that it is becoming easier for researchers to report vulnerabilities. As was mentioned in the 2022 report, Wordfence, along with other companies, became a CVE Numbering Authority (CNA) in 2021. This means that there are more points of contact for researchers to submit newly discovered vulnerabilities, and more bandwidth for processing vulnerability reports. As mentioned in the report, Wordfence hope to continue to amplify this trend with the launch of Wordfence Intelligence Community Edition, a complete free to access and utilize WordPress Vulnerability Database.
Conclusion
The increase in reported vulnerabilities illustrates more than ever the importance of keeping websites updated with the latest security updates. The increase seen in vulnerability reports is doing more than ever to keep WordPress secure, but this means that components may need to be updated more frequently as well. WordPress core, themes, and plugins should always be updated as quickly as possible after a new version is released to ensure that vulnerabilities are patched to minimize the chances of a threat actor being successful in their attack attempts. In addition to keeping websites updated, it is also important to implement a solution, like Wordfence, to protect your website from attacks and malware.
Wordfence Premium, Care and Response receive new firewall rules and malware signatures as soon as they are available, with new rules and signatures being available to Wordfence Free customers 30 days later. If you believe your site has been compromised as a result of these vulnerabilities, or any other vulnerability, Wordfence offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both of these products include hands-on support in case you need further assistance.
In addition to protecting your website, Wordfence Intelligence Community Edition provides the most up-to-date information on WordPress vulnerabilities, free of charge, helping you to stay on top of vulnerabilities that may affect your website.