While performing routine security research, one of Wordfence threat analysts discovered the latest version of a Command and Control (C2) script, which is referred to as F-Automatical within the script’s code and was commonly known as FoxAuto in older versions. This is the seventh version of this automatic C2 script that is developed and distributed by a threat group called Anonymous Fox. This script is exactly as advertised: a script that automates tasks performed by a threat actor on a compromised web server.
While this script is not used to exploit a vulnerability, it is a post-exploitation script that is run from a location under the threat actor’s control and can be used to maintain persistence or upload additional malware on a website that the threat actor has already accessed through an exploited vulnerability. Some of the malicious functions are built-in, while others are performed by downloading and running additional scripts from a hardcoded location.
Anonymous Fox is a threat group that was inspired by the works of Anonymous, but is not affiliated with the better-known hacktivists. Publicly, they are mainly focused on NFTs, however the group also has indicated a strong opposition to governments and large corporations, including Google and Amazon. In an interesting twist, their tools tend to be used against small businesses and individuals far more often than against corporations and governments.
The Fox Doesn’t Want You to Know What It Says
The initial script itself is only 6 lines of code, with a number of empty lines thrown in. The most important line in the script is line 17. This is where the entire malicious script actually resides, but encoded and compressed.
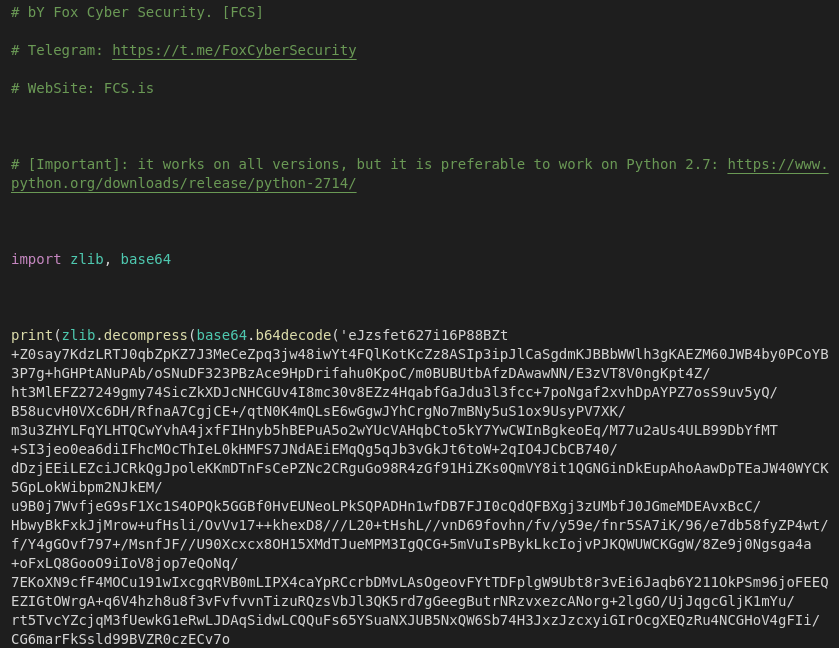
Once this line has been decompressed and decoded, Wordfence found a much larger script, consisting of more than 2,500 lines of code. The remaining obfuscation seems to be using an obscure method of encoding the text, based on a method developed by a Reddit user as a response to a challenge in the r/dailyprogrammer subreddit.
What the Fox Does
Without even fully decoding the script, we can see what this script does, thanks to a code block near the end. This block is the list that is printed to the screen, allowing the would-be attacker to choose which functions they will use during their attack attempt. The way this was coded indicates that the script author intended to distribute this malicious script to other threat actors.
The Fox Hides
Many of the functions are not built into this script. Common scripts and applications may be downloaded and installed from servers under the control of Anonymous Fox. Some of these uploads could be plugins (also known as extensions or modules in non-WordPress websites), or scripts like LeafMailer for sending emails, backdoors and shell scripts, configuration files, and even additional malware or other tools that may be of use to the threat actor.
The Fox Tracks
One of the pieces of information that led Wordfence to reversing the obfuscation in this script was the use of the Gyazo API, which was also used in previous versions of the script. The actual purpose of the API being used in this script is to take screenshots of successfully uploaded webshells and mailer scripts, typically used as proof when reselling access to a hacked site, and to save them in a searchable and web-accessible location. For obvious reasons, specific details are omitted here.
The Fox Replaces Your Locks
One thing that F-Automatical does differently from other scripts is resetting cPanel passwords instead of simply inserting new admin users. Many website administrators don’t access their cPanel dashboard frequently, which can help this password update to go unnoticed for an extended period of time.
The Fox Shows No Mercy
A portion of the script finds the website control panel and accesses a shell to give the threat actor the ability to run the commands of their choosing on an infected system. Once it has found the administrator panel, it configures a new shell connection that the threat actor can send malicious commands to the server through.
Conclusion
In this article, Wordfence broke down the F-Automatical script from Anonymous Fox, and showed several examples of what it can accomplish. This is the latest version of the script, which appears to be in active development, and has a much higher level of obfuscation than seen in previous versions. F-Automatical can be utilized to install additional malware, use the infected server to send malicious emails, or perform a complete takeover of a website, virtual server, or even a physical server in some cases.